My memories from childhood + imagination were enough for exactly one quest: a dozen tasks that are not duplicated.
But the children liked the fun, they asked for more quests and had to go online.
This article will not describe the script, legends, or design. But there will be 13 ciphers to encode the tasks for the quest.
Code number 1. Picture
A drawing or photo that directly indicates the place where the next clue is hidden, or a hint at it: broom + socket = vacuum cleanerComplication: make a puzzle by cutting the photo into several parts.
Code 2. Leapfrog.
Swap the letters in the word: SOFA = NIDAVCipher 3. Greek alphabet.
Encode the message using the letters of the Greek alphabet, and give the children the key:Code 4. Vice versa.
Write the assignment backwards:
- every word:
Etishchi dalk extra Jonsos - or an entire sentence, or even a paragraph:
Etsem morkom momas v - akzaksdop yaaschuudelS. itup monrev an yv
Code 5. Mirror.
(when I did the quest for my children, at the very beginning I gave them a “magic bag”: there was a key to the “Greek alphabet”, a mirror, “windows”, pens and sheets of paper, and all sorts of other unnecessary things for confusion. Finding the next riddle , they had to figure out for themselves what from the bag would help them find the answer)
Code 6. Rebus.
The word is encoded in pictures:
Cipher 7. Next letter.
We write a word, replacing all the letters in it with the following ones in alphabetical order (then I is replaced by A, in a circle). Or the previous ones, or the next ones after 5 letters :).
CABINET = SHLBH
Code 8. Classics to the rescue.
I took a poem (and told the children which one) and a code of 2 numbers: line number number of letters in the line.
Example:
Pushkin "Winter Evening"
The storm covers the sky with darkness,
Whirling snow whirlwinds;
Then, like a beast, she will howl,
Then he will cry like a child,
Then on the dilapidated roof
Suddenly the straw will rustle,
The way a belated traveler
There will be a knock on our window.
21 44 36 32 82 82 44 33 12 23 82 28
Did you read it, where is the hint? :)
Code 9. Dungeon.
Write the letters in a 3x3 grid:
Then the word WINDOW is encrypted like this:
Code 10. Labyrinth.
My children liked this code; it is unlike the others, because it is not so much for the brain, but for attention.
So:
On a long thread/rope you attach the letters in order, as they appear in the word. Then you stretch the rope, twist it and entangle it in every possible way between the supports (trees, legs, etc.). Having walked along the thread, as if through a maze, from the first letter to the last, the children will recognize the clue word.
Imagine if you wrap one of the adult guests in this way!
Children read - The next clue is on Uncle Vasya.
And they run to feel Uncle Vasya. Eh, if he is also afraid of tickles, then everyone will have fun!
Code 11. Invisible ink.
Use a wax candle to write the word. If you paint over the sheet with watercolors, you can read it.(there are other invisible inks... milk, lemon, something else... But I only had a candle in my house :))
Code 12. Rubbish.
The vowels remain unchanged, but the consonants change according to the key.For example:
SHEP SCHOMOZKO
reads as - VERY COLD, if you know the key:
D L X N H
Z M SCH K V
Code 13. Windows.
The kids loved it incredibly! They then used these windows to encrypt messages to each other all day long.So: on one sheet of paper we cut out windows, as many as there are letters in the word. This is a stencil, we apply it to a blank sheet of paper and write a clue word in the windows. Then we remove the stencil and write many different unnecessary letters on the remaining blank space of the sheet. You can read the code if you attach a stencil with windows.
The children were at first stupefied when they found a sheet covered with letters. Then they twisted the stencil back and forth, but you still need to put it on the right side!
Code 14. Map, Billy!
Draw a map and mark (X) the location with the treasure.When I did the quest for mine for the first time, I decided that the map was very simple for them, so I needed to make it more mysterious (then it turned out that just a map would be enough for the children to get confused and run in the opposite direction)...
This is the map of our street. Hints here are house numbers (to understand that this is actually our street) and huskies. This dog lives with a neighbor across the street.
The children did not immediately recognize the area and asked me leading questions..
Then 14 children took part in the quest, so I united them into 3 teams. They had 3 versions of this map and each one had its own place marked. As a result, each team found one word:
"SHOW" "FAIRY TALE" "TURNIP"
This was the next task :). He left behind some hilarious photos!
For my son’s 9th birthday, I didn’t have time to invent a quest, so I bought it on the MasterFuns website.. At my own peril and risk, because the description there is not very good.
But my children and I liked it because:
- inexpensive (similar to about 4 dollars per set)
- quickly (paid - downloaded, printed - everything took 15-20 minutes)
- There are a lot of tasks, with plenty to spare. And although I didn’t like all the riddles, there was plenty to choose from, and you could enter your own task
- everything is decorated in the same monster style and this gives the holiday effect. In addition to the quest tasks themselves, the kit includes: a postcard, flags, table decorations, and invitations to guests. And it's all about monsters! :)
- In addition to the 9-year-old birthday boy and his friends, I also have a 5-year-old daughter. The tasks were beyond her, but she and her friend also found entertainment - 2 games with monsters, which were also in the set. Phew, in the end - everyone is happy!
Surely, if you came to this site with the purpose decipher incomprehensible gobbledygook, the first question will be " How to solve this cipher?". Decipher the cipher(when you know cipher key And type of cipher) is easy, but decrypting the cipher (when you don’t know the key cipher, crack the code that is)... It's not easy, but with the help of this article and the CryptoApp application you can get an idea of cipher strength, determining the type cipher and perhaps even crack (decrypt) the cipher. Well, let's begin!
1. First you need to determine the type of cipher.
Determination methods:
a) if some encryption characters are used extremely often, while others are used extremely rarely (for example, in the following encryption" " (space) and the letter "F" are used very often, and the letter "Y" is used only once:
TSIPL ZHEVKFYO GZHALZH YZHKVZHRKNY YOK MKFN TSIPL ZHEVKFYOJJJ SHGDMY EJYJYNKVIMY LKMMBKSHKNY J YOKIAZHVDD YZHYOVYALYOLS1 IONDLDMYOS AND YZHYOYANYOS Ts IPLKS1 K NKBD YZHYOVYALISHZHRKNY BLKFED IONDLDMJD YLIVZHDOID1 YZHSHRZHVYAYUCHDD SHKTSIPLZHRKNY1 LKMTSIPLZHRRKNY AND GKD GDTSIPLZHRORKNY MZHACHDYIYA LKSHVIHYO EI RIGKEY TSIPLZHRKYIA AND ZHNYLKRVYANY TSIPLZHRBI R MZHUIKVIYOZhF MDNI RBZHENKBND2 YZHVOЪF MYIMZHB MNKNDF YZH TSIPLKE MEZHNLIND YIDD2 LDBZHEDOGODE YOKHKNY M RIG TSIPLZHR)
then most likely this is a simple substitution cipher (including its special cases Caesar Cipher, Affine Cipher, Atbash Cipher, etc.) or permutation cipher(Scitala et al.)
B) if there are several consecutive characters encryption are repeated in this encrypted message, (for example, in the following encryption, the sequence of characters “4ХБ” occurs three times:
! SH8SH-U!JTAUIU?F+NCFIOUБ!EVV4OY92FHQ9! ZАQ!P5JVTFQD9LCRMIS!SGIQЁY.B9ЭБМИ.X-ZG 4XBН2N4PSVE)RQВG 4XBШКЪ88ARKWHГTZKTMVD7MYШ?)+DDPSCAAKBEFGR L-LEMN8EXC2VCSK.WSQXЁ5C5ZMRN40FЗГИ3ГTZKTMEKЪ6EL.ZH.C BSIOALGPSE6X):VOVX96AJQIHZDCВ(L:ZPШW!4UBDEJ.KЖL).EG5,G QPKGMRK:LVP6ШVPEQJ9L8:Z-3,K, 4XBШТъ6G8ДКжL).T6
then most likely this is the Vigenère Cipher
C) if none of the above methods determining the type of cipher didn’t fit, you’ll have to guess it - to make your fate easier codebreaker- Types of ciphers
2. Having determined type of cipher(or assuming that we have determined it) - read the article Decryption
Or an article specifically on this type of encryption. And if this is a simple substitution cipher, a Vigenère cipher, then you will certainly need a free tool for deciphering these types of ciphers- CryptoApp application. Now if you are asked how to solve the code, you will already have a clear algorithm of actions!
Since there are a huge number of ciphers in the world, it is impossible to consider all the ciphers not only within the framework of this article, but also the entire website. Therefore, we will consider the most primitive encryption systems, their application, as well as decryption algorithms. The goal of my article is to explain to a wide range of users the principles of encryption/decryption in the most accessible way possible, as well as to teach primitive ciphers.
Back at school, I used a primitive cipher, which my older comrades told me about. Let's consider the primitive cipher “Cipher with letters replaced by numbers and vice versa.”
Let's draw a table, which is shown in Figure 1. We arrange the numbers in order, starting with one and ending with zero horizontally. Below the numbers we substitute arbitrary letters or symbols.
Rice. 1 Key to the cipher with replacement of letters and vice versa.
Now let's turn to table 2, where the alphabet is numbered. 
Rice. 2 Table of correspondence between letters and numbers of alphabets.
Now let's encrypt the word C O S T E R:
1) 1. Let's convert letters into numbers: K = 12, O = 16, C = 19, T = 20, E = 7, P = 18
2) 2. Let’s convert the numbers into symbols according to Table 1.
KP KT KD PSH KL
3) 3. Done.
This example shows a primitive cipher. Let's look at fonts that are similar in complexity.
1. 1. The simplest cipher is the CIPHER WITH REPLACEMENT OF LETTERS BY NUMBERS. Each letter corresponds to a number in alphabetical order. A-1, B-2, C-3, etc.
For example, the word “TOWN” can be written as “20 15 23 14”, but this will not cause any particular secrecy or difficulty in deciphering.
2. You can also encrypt messages using a NUMERIC TABLE. Its parameters can be anything, the main thing is that the recipient and sender are aware. Example of a digital table. 
Rice. 3 Digital table. The first digit in the cipher is a column, the second is a row, or vice versa. So the word “MIND” can be encrypted as “33 24 34 14”.
3. 3. BOOK CIPHER
In such a cipher, the key is a certain book that is available to both the sender and the recipient. The cipher indicates the page of the book and the line, the first word of which is the solution. Decryption is impossible if the sender and the correspondent have books of different years of publication and issue. The books must be identical.
4. 4. CAESAR CIPHER(shift cipher, Caesar shift)
Well-known cipher. The essence of this cipher is the replacement of one letter with another, located at a certain constant number of positions to the left or right of it in the alphabet. Gaius Julius Caesar used this encryption method when corresponding with his generals to protect military communications. This cipher is quite easy to crack, so it is rarely used. Shift by 4. A = E, B= F, C=G, D=H, etc.
An example of a Caesar cipher: let's encrypt the word “DEDUCTION”.
We get: GHGXFWLRQ. (shift by 3)
Another example:
Encryption using key K=3. The letter "C" "shifts" three letters forward and becomes the letter "F". A hard character moved three letters forward becomes the letter “E”, and so on:
Original alphabet: A B C D E F G H H I J J K L M N O P R S T U V X C
Encrypted: G D E E F G H I J K L M N O P R S T U V
Original text:
Eat some more of these soft French rolls and drink some tea.
Ciphertext is obtained by replacing each letter of the original text with the corresponding letter of the cipher alphabet:
Fezyya yz zyi ahlsh pvenlsh chugrschtskfnlsh dsosn, zhg eyutzm ygb.
5. CIPHER WITH CODE WORD
Another simple method in both encryption and decryption. A code word is used (any word without repeating letters). This word is inserted in front of the alphabet and the remaining letters are added in order, excluding those that are already in the code word. Example: code word – NOTEPAD.
Original: A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
Replacement: N O T E P A D B C F G H I J K L M Q R S U V W X Y Z
6. 6. ATBASH CIPHER
One of the simplest encryption methods. The first letter of the alphabet is replaced by the last, the second by the penultimate, etc.
Example: "SCIENCE" = HXRVMXV
7. 7. FRANCIS BACON CIPHER
One of the simplest encryption methods. Encryption uses the Bacon cipher alphabet: each letter of a word is replaced by a group of five letters "A" or "B" (binary code).
a AAAAAA g AABBA m ABABB s BAAAB y BABBA
b AAAAB h AABBB n ABBAA t BAABA z BABBB
c AAABA i ABAAA o ABBAB u BAABB
d AAABB j BBBAA p ABBBA v BBBAB
e AABAA k ABAAB q ABBBB w BABAA
f AABAB l ABABA r BAAAA x BABAB
The difficulty in decrypting lies in determining the cipher. Once it is determined, the message is easily alphabetized.
There are several coding methods.
It is also possible to encrypt the sentence using binary code. The parameters are determined (for example, “A” - from A to L, “B” - from L to Z). So BAABAAAAABAAAABABABB stands for TheScience of Deduction! This method is more complicated and tedious, but much more reliable than the alphabetical option.
8. 8. BLAISE VIGENERE CIPHER.
This cipher was used by the Confederates during the Civil War. The cipher consists of 26 Caesar ciphers with different shift values (26 letters of the Latin alphabet). A tabula recta (Vigenère square) can be used for encryption. Initially, the key word and the source text are selected. The word key is written cyclically until it fills the entire length of the source text. Further along the table, the letters of the key and the original text intersect in the table and form the ciphertext.

Rice. 4 Blaise Vigenere Cipher
9. 9. LESTER HILL CIPHER
Based on linear algebra. It was invented in 1929.
In such a cipher, each letter corresponds to a number (A = 0, B = 1, etc.). A block of n-letters is treated as an n-dimensional vector and multiplied by an (n x n) matrix mod 26. The matrix is the cipher key. To be decryptable, it must be reversible in Z26n.
In order to decrypt a message, you need to turn the ciphertext back into a vector and multiply by the inverse key matrix. For detailed information, Wikipedia can help.
10. 10. TRITEMIUS CIPHER
Improved Caesar cipher. When decoding it is easiest to use the formula:
L= (m+k) modN , L-number of the encrypted letter in the alphabet, m-ordinal number of the letter of the encrypted text in the alphabet, k-shift number, N-number of letters in the alphabet.
It is a special case of an affine cipher.
11. 11. MASONIC CIPHER


12. 12. GRONSFELD CIPHER
In terms of its content, this cipher includes the Caesar cipher and the Vigenère cipher, but the Gronsfeld cipher uses a numerical key. Let's encrypt the word “THALAMUS” using the number 4123 as a key. We enter the numbers of the numerical key in order under each letter of the word. The number under the letter will indicate the number of positions by which the letters need to be shifted. For example, instead of T you get X, etc.
T H A L A M U S
4 1 2 3 4 1 2 3
T U V W X Y Z
0 1 2 3 4
As a result: THALAMUS = XICOENWV
13. 13. PIG LATIN
More often used as children's fun, it does not cause any particular difficulty in deciphering. The use of English is mandatory, Latin has nothing to do with it.
In words that begin with consonants, those consonants are moved back and the “suffix” ay is added. Example: question = questionquay. If the word begins with a vowel, then ay, way, yay or hay is simply added to the end (example: a dog = aay ogday).
In Russian, this method is also used. They call it differently: “blue tongue”, “salty tongue”, “white tongue”, “purple tongue”. Thus, in the Blue language, after a syllable containing a vowel, a syllable with the same vowel is added, but with the addition of a consonant “s” (since the language is blue). Example: Information enters the nuclei of the thalamus = Insiforsomasatsiyasya possotussupasaetse v yadsyarasa tasalasamususasa.
Quite an exciting option.
14. 14. POLYBIUS SQUARE
Similar to a digital table. There are several methods for using the Polybius square. An example of a Polybius square: we make a 5x5 table (6x6 depending on the number of letters in the alphabet).

1 METHOD. Instead of each letter in a word, the corresponding letter below is used (A = F, B = G, etc.). Example: CIPHER - HOUNIW.
2 METHOD. The numbers corresponding to each letter from the table are indicated. The first number is written horizontally, the second – vertically. (A = 11, B = 21...). Example: CIPHER = 31 42 53 32 51 24
3 METHOD. Based on the previous method, we will write the resulting code together. 314253325124. Shift left one position. 142533251243. Again we divide the code in pairs. 14 25 33 25 12 43. As a result, we get the cipher. The pairs of numbers correspond to the letter in the table: QWNWFO.
There are a great variety of ciphers, and you can also come up with your own cipher, but it is very difficult to invent a strong cipher, since the science of decryption has stepped far forward with the advent of computers and any amateur cipher will be cracked by specialists in a very short time.
Methods for opening mono-alphabetic systems (decoding)
Despite their simplicity in implementation, mono-alphabetic encryption systems are easily vulnerable.
Let us determine the number of different systems in an affine system. Each key is completely defined by a pair of integers a and b, specifying the mapping ax+b. There are j(n) possible values for a, where j(n) is the Euler function returning the number of coprime numbers with n, and n values for b that can be used regardless of a, except for identity mapping (a=1 b =0), which we will not consider.
This gives j(n)*n-1 possible values, which is not that many: with n=33 a can have 20 values (1, 2, 4, 5, 7, 8, 10, 13, 14 , 16, 17, 19, 20, 23, 25, 26, 28, 29, 31, 32), then the total number of keys is 20*33-1=659. Searching through such a number of keys will not be difficult when using a computer.
But there are methods that simplify this search and that can be used when analyzing more complex ciphers.
Frequency analysis
One such method is frequency analysis. The distribution of letters in the cryptotext is compared with the distribution of letters in the alphabet of the original message. The letters with the highest frequency in the cryptotext are replaced by the letter with the highest frequency from the alphabet. The probability of a successful attack increases with increasing cryptotext length.
There are many different tables about the distribution of letters in a given language, but none of them contains definitive information - even the order of letters may differ in different tables. The distribution of letters depends very much on the type of test: prose, spoken language, technical language, etc. The laboratory work instructions provide frequency characteristics for various languages, from which it is clear that the letters I, N, S, E, A (I, N, S, E, A) appear in the high-frequency class of each language.
The simplest defense against frequency-counting attacks is provided by the system of homophones (HOMOPHONES) - monophonic substitution ciphers in which one plaintext character is mapped onto several ciphertext characters, their number proportional to the frequency of occurrence of the letter. When encrypting the letter of the original message, we randomly select one of its replacements. Therefore, simply counting frequencies does not give the cryptanalyst anything. However, information is available on the distribution of pairs and triplets of letters in various natural languages.
Instructions
In modern terms, any encrypted message has an author who composed it; the addressee for whom it is intended; and the interceptor - the cryptographer trying to read it.
There are two main methods used in manual encryption: substitution and permutation. The first is that the letters of the original message are replaced by others according to a certain rule. The second is that the letters, again according to the rule, change places. Of course, these two methods can be combined, which makes the cipher more secure.
The simplest type of substitution cipher is cryptography. In this case, the letters are replaced by conventional icons: numbers, symbols, images of dancing men, and so on. To reveal a secretly written message, it is enough to determine which symbol corresponds to which letter.
For this purpose, frequency tables are usually used, showing how often a particular letter occurs in the language of the message. For example, in a language, the first places in such a table will be the letters “a”, “e”, “o”. By substituting them instead of the most frequently encountered icons, you can decipher some words, and this, in turn, will give the meanings of other symbols.
In more secure ciphers, letters are replaced using a key. For example, the key can be a multi-digit number. To encrypt text in this way, a key number is written over it many times so that there is a number above each letter. After this, the letter is replaced by another, the one following it through as many positions as indicated by the number. In this case, the alphabet is considered closed in a ring, that is, for example, the second letter after “i” will be “b”.
It is more difficult to open such a cryptogram, since for each letter of the cipher there are ten reading options. To decrypt, you must first determine the length of the key and divide the text into words. This is usually done using a table, where the first line is the encryption text, and below it are options where each letter of the cipher is replaced with a possible letter of the original text. Thus, the table has eleven lines.
By looking at which options lead to the most natural-looking division of the text into words, the cryptographer determines what letters are used to encode spaces, and therefore finds one or more digits of the key. From this you can already begin to draw conclusions about how many times the key is repeated in the text.
By substituting options from the table in place of as yet unknown letters, the cryptographer determines in which cases meaningful words and fragments appear in the text.
To make his work easier, the cryptographer usually seeks to find out any information about the contents of the text or key. If you know what signature is at the end of the document, or what word should be repeated there often, then using this information you can reveal part of the encryption key. By substituting the found fragment in other places in the document, the cryptographer finds out the length of the key and learns several more parts of the source text.
Video on the topic
Sources:
- Vladimir Zhelnikov. Cryptography from papyrus to computer
- how to replace letters with symbols
Decoding is one of the most exciting activities. After all, it is always so curious to find out what exactly is hidden behind this or that encoding. Moreover, there are very, very many types of different ciphers. Therefore, there are also plenty of ways to recognize and translate them. The most difficult task is to correctly determine exactly how to decipher a particular riddle.
Instructions
If you are going to decrypt a specific encoding, remember that in most cases information is encrypted through substitution. Try to identify the most common letters in the language and match them with the ones you have in the code. Researchers have made your task easier and have already compiled some of them into a table. If you use it, it will significantly speed up the decryption process. In a similar way, at one time they were solved ciphers Polybius and Caesar.
To make it easier to study, use the keys. To decrypt, you will need a concept like the length of the key, which you can only determine by selecting individual letters (see step 1). Once you select the length of your key, you can form a group of characters that is encoded with one letter. And so gradually the whole code will be revealed to you. This process is quite labor-intensive and time-consuming, so please be patient.
Also try to decipher the message by selecting one word that is likely to appear in this text. Shift it across the text until it overlaps itself in the cipher. This way you will define part of the key. Next, decipher the text in the area around the key. Select text decoding options accordingly. It must necessarily correlate with the key word and be adequate to it, i.e. match the context.
Remember that to successfully decipher the encoding, you will need knowledge of the most well-known message encryption methods. So, for example, if you have a text dating from the 5th century BC, then with a high degree of probability we can say that it is encoded in a wandering. The principle of such encryption was the method of simple permutation. That is, the letters of the alphabet simply swapped places and then, using a round object, were applied to the sheet in a chaotic order. To decipher such a message, the main thing is to correctly restore the size of this round object.
Recognize digital encryption using mathematical methods. One popular way is to use probability theory. And in the Middle Ages, using mathematical symbols, it was done by rearranging and using magic squares. These are figures in which the numbers fit into the cells as successive natural numbers. As a rule, they start with 1. The secret of the magic square is that all the numbers in it, in the sum of each column or row, or diagonal, give the same number.
Take into account the fact that the text for decryption is located in such a square according to the numbering of the cells. Write down the contents of the table and get the text that needs to be decrypted. And only then, by rearranging, select the required encryption option.
The fashion for deciphering words is quickly spreading on the Internet. Some people sincerely believe in the meaning of this action, others are openly having fun. In both cases we are talking about solving puzzles. Only the rules of the puzzle may be different.

Man is a social being. We learn to interact with others by observing their reactions to our actions from the first days of life. In any interaction, we use what art historians call “cultural codes.” But cultural codes are the most difficult to decipher; there is no special program that will tell you what a raised eyebrow or seemingly causeless tears can mean; there is no clear answer; Moreover, even the “encoder” himself may not know what he meant by his action! The science of understanding others is something that we comprehend throughout our lives, and the better this skill is developed, the more harmonious, as a rule, is communication with others and any activity that requires coordinated actions.
Studying cryptography in both its forms (encryption and decryption) allows you to learn how to find a connection between an encrypted, confusing, incomprehensible message and the meaning that is hidden in it. Walking the historical path from the Julius Caesar cipher to RSA keys, from the Rosetta Stone to Esperanto, we learn to perceive information in an unfamiliar form, solve riddles, and get used to multivariance. And most importantly, we learn to understand: both different people, unlike us, and the mathematical and linguistic mechanisms that underlie each, absolutely each message.
So, an adventure story about cryptography for children, for everyone who has children, and for everyone who has ever been a child.
Flags flutter in the wind, hot horses neigh, armor rattles: it was the Roman Empire who discovered that there was still someone in the world whom they had not conquered. Under the command of Gaius Julius Caesar there is a huge army that must be quickly and accurately controlled.
Spies are not asleep, enemies are preparing to intercept the emperor's envoys in order to find out all his brilliant plans. Every piece of parchment that falls into the wrong hands is a chance of losing the battle.
But then the messenger is captured, the attacker unfolds the note... and understands nothing! “Probably,” he scratches the back of his head, “it’s in some unknown language...” Rome triumphs, its plans are safe.
What is the Caesar cipher? Its simplest version is when instead of each letter we put the next one in the alphabet: instead of “a” - “b”, instead of “e” - “z”, and instead of “i” - “a”. Then, for example, “I like to play” will become “A mävmä ydsbue.” Let's look at the sign; at the top there will be a letter that we encrypt, and at the bottom there will be a letter with which we replace it.
The alphabet is sort of “shifted” by one letter, right? Therefore, this cipher is also called a “shift cipher” and they say “we use the Caesar cipher with a shift of 10” or “with a shift of 18”. This means that we need to “shift” the lower alphabet not by 1, like ours, but, for example, by 10 - then instead of “a” we will have “th”, and instead of “y” we will have “e”.
Caesar himself used this cipher with a shift of 3, that is, his encryption table looked like this:
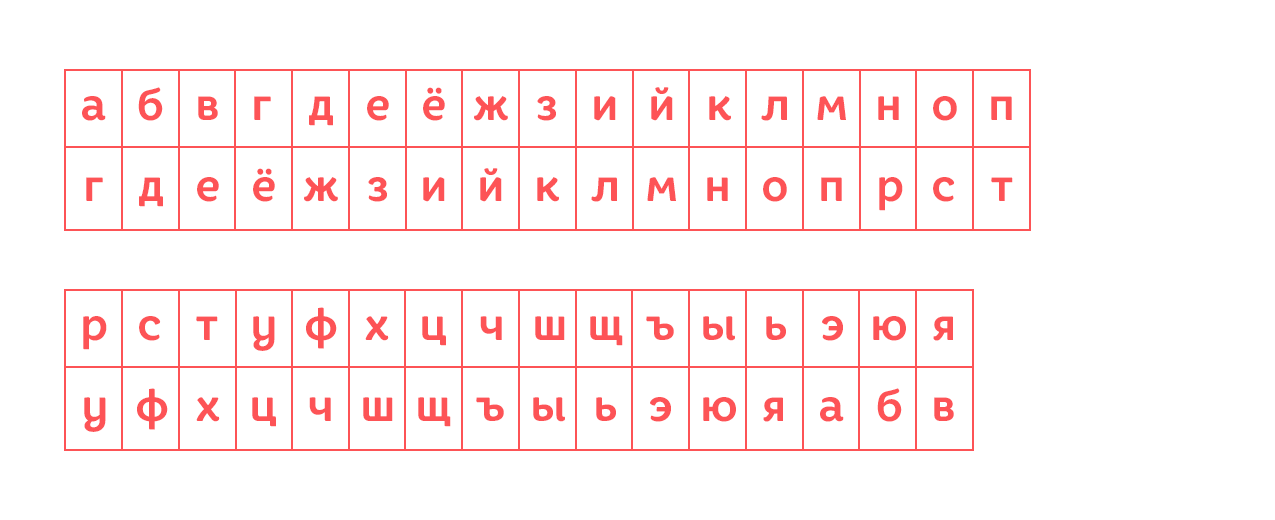
More precisely, she would have looked like this if Caesar lived in Russia. In his case, the alphabet was Latin.
Such a cipher is quite easy to crack if you are a professional spy or Sherlock Holmes. But he is still suitable for keeping his little secrets from prying eyes.
You yourself can arrange your own little home plot. Agree on your shift number, and you can leave coded notes on each other's refrigerator for a surprise for someone's birthday, send coded messages, and maybe, if you're separated for a long time, even write secret, coded letters to each other!
But the whole history of cryptography is the history of the struggle between the art of encrypting messages and the art of deciphering them. When a new way to encode a message appears, there are those who try to break this code.
What is "crack the code"? This means coming up with a way to solve it without knowing the key and meaning of the cipher. The Caesar cipher was also once cracked using the so-called “frequency analysis method.” Look at any text - there are many more vowels in it than consonants, and there are much more “o” than, for example, “I”. For each language, you can name the most frequently and rarely used letters. You just need to find which letter is the most in the ciphertext. And most likely it will be an encrypted “o”, “e”, “i” or “a” - the most common letters in Russian words. And as soon as you know what letter is used to denote, for example, “a,” you know how much the encrypted alphabet is “shifted,” which means you can decipher the entire text.
When the whole world learned the solution to Caesar's code, cryptographers had to come up with something more powerful. But, as often happens, people did not invent something completely new, but complicated what already existed. Instead of encrypting all the letters using the same shifted alphabet, several of them began to be used in secret messages. For example, we encrypt the first letter of the alphabet with a shift of 3, the second - with a shift of 5, the third - with a shift of 20, the fourth - again with a shift of 3, the fifth - with a shift of 5, the sixth - with a shift of 20, and so on, in a circle. Such a cipher is called polyalphabetic (that is, multi-alphabetic). Try it, your cipher can only be solved by someone who is privy to the secrets of cryptography!
It would seem that the attackers should have become confused and the secrets should have remained secrets forever. But if the cipher has been cracked once, then any more complex versions of it will also be cracked once.
Let's imagine that someone encrypted a message in two alphabets. The first letter is with a shift of 5, the second is with a shift of 3, the third is again 5, the fourth is again 3 - as on the plate below.

We can divide all encrypted letters into two groups: letters encrypted with a shift of 5 (1, 3, 5, 7, 9, 11, 13, 15, 17, 19) and letters encrypted with a shift of 3 (2, 4, 6 , 8, 10, 12, 14, 16, 18, 20). And within each group, look for which letters we encountered more often than others - just like in the Caesar cipher, only more hassle.
If the coder used three alphabets, then we will divide the letters into three groups, if five, then into five. And then the same frequency analysis comes into play again.
You can ask the question - how did the decryptors know that there were three alphabets, and not, for example, five? They didn't really know. And we looked through all possible options. Therefore, decryption took much longer, but was still possible.
In cryptography, the message to be transmitted is called "plaintext" and the encrypted message is called "ciphertext". And the rule by which the text is encrypted is called the “cipher key”.
The 20th century crept up unnoticed. Humanity is relying more and more on cars: trains are replacing carts, radios are appearing in almost every home, and the first airplanes have already taken flight. And the encryption of secret plans is also eventually transferred to machines.
During World War II, many machines were invented to encrypt messages, but they all relied on the idea that a polyalphabetic cipher could be further obfuscated. To confuse it so much that, although in theory it could be solved, in practice no one will succeed. Confuse as much as a machine can do, but a person cannot. The most famous of these encryption machines is Enigma, used by Germany.

theromanroad.files.wordpress.com
But while Germany’s most important secret was the design of Enigma, the most important secret of its opponents was that by the middle of the war all countries had already solved Enigma. If this had become known in Germany itself, they would have started to come up with something new, but until the end of the war they believed in the ideality of their encryption machine, and France, England, Poland, Russia read secret German messages like an open book.
The thing is that the Polish scientist Marian Rejewski once thought that since they had invented a machine for encrypting messages, they could also invent a machine for decrypting them, and he called his first sample “Bomb”. Not because of the “explosive” effect, as one might think, but in honor of the delicious, round cake.
Then the mathematician Alan Turing built on its basis a machine that completely deciphered the Enigma code, and which, by the way, can be considered the first progenitor of our modern computers.

The most complex code of the entire Second World War was invented by the Americans. Each US warship was assigned... an Indian. Their language was so incomprehensible and poorly understood, it sounded so strange that the codebreakers did not know how to approach it, and the US Navy fearlessly transmitted information in the language of the Choctaw Indian tribe.
In general, cryptography is not only about how to solve a riddle, but also about how to solve it. People don’t always come up with such riddles on purpose; sometimes history itself throws them up. And one of the main mysteries for cryptographers for a long time was the mystery of the ancient Egyptian language.

Nobody knew what all these hieroglyphs meant. What did the Egyptians mean when they painted birds and scarabs? But one lucky day, the French army discovered the Rosetta Stone in Egypt.

There was an inscription on this stone - the same one, in ancient Greek, Egyptian alphabetic (demotic text) and Egyptian hieroglyphic. Historians of that time knew ancient Greek well, so they quickly learned what was written on the stone. But the main thing is that, knowing the translation, they were able to reveal the secrets of the ancient Egyptian language. The demotic text was deciphered quickly enough, but historians, linguists, mathematicians, and cryptographers puzzled over the hieroglyphs for many years, but in the end they finally figured it out.
And this was a great victory for cryptographers - a victory over time itself, which hoped to hide their history from people.
But among all these solved ciphers, there are three special ones. One is the Diffie–Hellman method. If a small message is encrypted using this method, then in order to decrypt it, you need to take all the computers in the world and keep them busy for many, many years. This is what is used on the Internet today.
The second is quantum encryption. True, it has not yet been completely invented, but if people make quantum computers the way they dream of them, then such a code will know when they are trying to decrypt it.
And the third special cipher is the “book cipher”. Its amazingness is that it is easy for them to encrypt something and not easy for them to decrypt it. Two people choose the same book, and each word in their writing is searched for and replaced with three numbers: the page number, the line number, and the word number in the line. It's very easy to do, right? And it’s not at all easy to solve: how does a spy know which book you chose? And most importantly, computers won’t help much in this matter either. Of course, if you connect a lot of smart people and a lot of powerful computers, such a cipher will not stand.
But there is a main safety rule. There should be so much of this security that the encrypted message is not worth the enormous effort that must be spent on deciphering it. That is, so that the villain - the spy - would have to spend as much effort to unravel your code as he is not willing to spend to find out your message. And this rule works always and everywhere, both in friendly school correspondence and in the world of real spy games.
Cryptography is the art of making and solving riddles. The art of keeping secrets, and the art of revealing them. With cryptography, we learn to understand each other and figure out how to keep something important to ourselves safe. And the better we are at both, the calmer and more active our life can be.









