Federal agency State by education educational institution higher professional education Nizhny Novgorod state university them. N.I. Lobachevsky Faculty of Computational Mathematics and Cybernetics Department of Informatics and Automation scientific research Textbook for the course COMPUTING SYSTEMS, NETWORKS AND TELECOMMUNICATIONS Section INFORMATION COMPUTING NETWORKS Part 1 Nizhny Novgorod 2008 Information and computing networks. Study guide. Part 1 // N. Novgorod, Nizhny Novgorod State University, 2008. In textbook presents material for the course “Computer systems, networks and telecommunications”, section “Information and computing networks”. The first part of the manual contains basic information on the basics of network technologies. Are being considered general questions related to the organization of computer networks, the OSI model, principles of data transfer. Compiled by: Art. teacher of the department IANI Faculty of VMK, Ph.D. Kumagina E.A. 2 Contents 1. GENERAL PRINCIPLES OF ORGANIZING COMPUTER NETWORKS......... 4 1.1. PREREQUISITES FOR THE DEVELOPMENT AND EVOLUTION OF COMPUTER NETWORKS.................................................... 4 1.2. THE CONCEPT OF COMPUTER NETWORK................................................................. ................................... 5 1.3. AF COMPONENTS................................................... ........................................................ .......... 5 1.4. Peer-to-Peer LANs AND LANs WITH DEDICATED SERVERS.................................................... 7 1.5 . LAN TOPOLOGY................................................... ........................................................ .......... 8 2. OPEN SYSTEMS AND PROBLEMS OF STANDARDIZATION...................... 11 2.1. LEVELS OF NETWORK ARCHITECTURE.................................................... .................................... 11 2.2. SOURCES OF NETWORK STANDARDS.................................................................. ........................... 13 2.3. OPEN SYSTEMS NETWORKS.................................................................. ............................................... 14 2.4. OSI MODEL ................................................... ........................................................ .................. 14 3. COMMUNICATION LINES.................................... ........................................................ ................................ 20 3.1. CHARACTERISTICS OF COMMUNICATION LINES.................................................... .................................... 21 3.2. CABLES......................................................... ........................................................ ....................... 23 4. PHYSICAL CODING METHODS.................................... ................................... 26 4.1. ANALOG MODULATION................................................................. ............................................... 26 4.2. DIGITAL CODING................................................................. ............................................... 27 4.3. LOGIC CODING................................................................. ........................................... 29 4.4. DISCRETE MODULATION OF ANALOG SIGNALS. ........................................................ 30 5. METHODS OF DATA TRANSMISSION OF CHANNEL LEVEL.................................... 31 5.1. ASYNCHRONOUS AND SYNCHRONOUS DATA TRANSFER.................................... .................... 31 5.2. CHANNEL AND PACKET SWITCHING.................................................... ........................... 32 5.3. PRINCIPLES OF MULTIPLEXING.................................................................... ........................... 36 5.4. ERROR DETECTION AND CORRECTION.................................................................... ............................... 37 6. LITERATURE .................. ........................................................ ............................................... 38 3 1. General principles organization of computer networks 1.1. Prerequisites for the development and evolution of computer networks The concept of computer networks is a logical result of the evolution of computer technologies and telecommunications. 50s. The first computers were very bulky. They weren't intended for interactive work, but worked in batch mode. The programmer typed the program text onto punched cards, took them to the computer center, and the next day received a printed result. This approach made the most efficient use of processor time. The mainframes are not gone. Now they are used because one super-powerful computer is easier to maintain and maintain than several less powerful ones. 60s. Appeared new way organization of the computing process. Interactive multi-terminal time sharing systems began to develop. There is one processor, several terminals are connected to it. The system response time was fast enough that the user did not notice parallel work with other users. Provided access to shared files and peripheral devices. This is outwardly very similar to a LAN, but such a system has a centralized data processing nature. Now this principle is used, for example, by ATM networks. At this time, there was a need to unite computers located at a distance from each other. long distance. It began with solving the problem of connecting a terminal to a computer located hundreds of kilometers away. This was done through telephone lines using modems. Such systems allowed users to receive remote access to shared resources of powerful computers. Then computer-to-computer communications were implemented. Computers have gained the ability to exchange data automatically, and this is already a basic mechanism in the aircraft. Thus, using this mechanism, file sharing services were implemented, by email, database synchronization, etc. 70s. There was a technological breakthrough in the field of computer production - large integrated circuits appeared. The first mini-computers appeared. Their cost was constantly decreasing, and now even small departments of enterprises were able to have computers. Now there were many disparate computers in one enterprise. There was a need to exchange data between nearby computers. This is how the first LANs were formed. The software and interface devices necessary for the computers to communicate were developed. The difference from modern LANs is that connections were made using a variety of non-standard devices with their own methods of presenting data on the line and with their own cables. These devices could only connect to the types of computers for which they were designed. 80s. Widespread use of personal computers. They have become ideal elements for building networks. On the one hand, they were powerful enough to operate a network software, and on the other hand, their power was not enough to solve complex tasks. Standard technologies for connecting computers into an Ethernet network, Arcnet, and Token Ring have been established. 4 Current trends development of aircraft Instead of passive cable, more complex communication equipment (switches, routers) is used. Usage large computers(mainframes). Transmission of a new type of information (voice, video image). Changes are needed in protocols and OS so that there are no delays in the transfer of information. Delays when transferring files or mail are not so critical. The emergence of new wireless communication methods. Merger of networks (local and global) and technologies (computer networks, telephone networks, television networks) thanks to the advent of IP technologies. 1.2. The concept of a computer network A computer network is a collection of computers connected by communication lines. Network nodes are end or intermediate devices that have a network address. These are workstations or servers (computers with a network interface), peripheral devices (printer, plotter, scanner), network telecommunication devices (shared modem) and routers. Communication lines are formed by cables, network adapters and other communication devices. All network equipment operates under the control of system and application software. Thanks to computer networks, users have the opportunity to share resources, programs and data from all computers. The concept of local area network - LAN (English LAN - Lokal Area Network) refers to geographically limited (territorially or production) hardware and software implementations, in which several computer systems are connected with each other using appropriate means of communication. Thanks to this connection, the user can interact with other workstations connected to this LAN. Local networks can be combined into larger networks - CAN (Campus Area Network). This is a network located in nearby buildings. Larger networks are city-scale networks (MAN, Metropolian Area Network) and large-scale networks (GAN, Global Area Network). Local networks are characterized by more high speed data transmission from 10 Mbit/s and the fact that a special cable system is usually laid for them. Global networks use already laid communication lines and transmission speeds in them are significantly lower. 1.3. Aircraft components 1. Hardware platform Computers. From personal computers to super computers. The set of computers must correspond to the class of problems solved by the network. Communication equipment. Although computers are central to information processing on a network, communications equipment plays a role too important role. These are cable systems, repeaters, bridges, switches, routers, modular hubs. They affect both the characteristics of the network and its cost. 2. Network software platform Operating systems. The efficiency of the network depends on which concepts for managing local and distributed resources form the basis of the network OS. (Novell NetWare, Windows NT) Network applications. Most top layer network tools are various network applications: network databases, mail systems, teamwork automation systems, etc. Table 1. Computer components Applications of the subject area (accounting, computer-aided design, management technological processes etc.) System services (www, e-mail, file, Multimedia software platform, IP telephony, e-commerce) DBMS Network operating systems Transport system Hardware platform Computers Question: when is a network needed? The introduction of a network at an enterprise should ultimately increase the efficiency of its operation, which will be reflected in an increase in profits. IN production practice The sun plays a very important role. Through a LAN, the system integrates personal computers located at many remote workplaces, which share equipment, software and information. Employees' workplaces are no longer isolated and are combined into a single system. Let's consider the advantages obtained by networking personal computers compared to stand-alone computers or multi-machine systems. 1. Opportunity sharing data and devices. This provides quick access to extensive corporate information, which allows you to make quick and high-quality decisions. Sharing resources allows them to be used economically, for example, to control peripheral devices such as laser printers from all connected workstations. Shared resources include disk space, printers, modems, and fax modems. Software separation provides the ability to simultaneously use centralized, previously installed software. Although the operation of such an application will slow down somewhat (it takes time to transfer data over the network), this approach will make the administration and support of the application easier. By sharing processor resources, it is possible to use computing power to process data by other systems on the network. The opportunity provided is that the available resources are not “attacked” instantly, but only through a special processor available to each workstation. 2. Improving communications. This is an improvement in the process of information exchange between enterprise employees, clients, and suppliers. Networks reduce the need for businesses to use other forms of information transmission (telephone or regular mail). New technologies make it possible to transmit not only computer data, but also video information. There is no need to talk about email programs, chats, schedulers. 3. High fault tolerance. This is the ability of the system to perform its functions in the event of failure of individual hardware elements and incomplete data availability. The basis for this is the redundancy of the processing nodes. If a node fails, its tasks are reassigned to other nodes. Data sets can be duplicated on the VRAM of several computers on the network, so that if one of them fails, the data continues to be available. 4. Ability to perform parallel calculations. Due to this, in a system with several nodes, performance can be achieved that exceeds the performance of a single processor. 1.4. Peer-to-peer LANs and LANs with dedicated servers There are two approaches to organizing network software. LANs are divided into two fundamentally different classes: peer-to-peer (single-level) networks and hierarchical (multi-level). When working on a network, a computer can provide its resources to network users (server), and can access network resources (client). Peer-to-peer networks A peer-to-peer network is a network of peer computers (equal access rights to each other's resources). Network management functions are transferred in turn from one station to another. Typically, workstations have access to the disks of other stations. It is advisable to use peer-to-peer networks if there is intensive data exchange between stations. In peer-to-peer networks, all computers have equal access rights to each other's resources. Each user can, at his own discretion, declare any resource on his computer to be shared, after which other users can exploit it. In such networks, the same OS is installed on all computers, which provides potentially equal capabilities to all computers on the network. In peer-to-peer networks, functional asymmetry can also arise: some users do not want to share their resources with others, and in this case their computers act as a client. The administrator has assigned only functions for organizing the sharing of resources to other computers, which means they are servers. In the third case, when a local user does not object to the use of his resources and does not exclude the possibility of accessing other computers, the OS installed on his computer must include both server and client parts. Unlike networks with dedicated servers, in peer-to-peer networks there is no OS specialization depending on the predominant functional focus - client or server. All variations are implemented by configuring the same OS version. The advantage of a peer-to-peer network is ease of maintenance (these are the functions of a system administrator). However, these networks are used mainly to unite small groups of users who do not have great requirements for the volume of stored information, its security from unauthorized access and access speed. Hierarchical networks With increased requirements for these characteristics, two-rank networks (hierarchical, with a dedicated server) are more suitable, where the server better solves the problem of serving users with its resources, since its equipment and network operating system specially designed for this purpose. The type of server is determined by the many tasks for which it is intended: file server – storing data and managing access to it print server – managing the printer and access to it security server – ensures the functioning of the resource protection system, stores information about devices and for users, application server – performs the computing parts of client-server applications; mail server – is responsible for the functioning of email. 1.5. LAN topology Topology (topos - place, logos - doctrine) is a branch of mathematics that studies ways to connect different entities. In relation to computer networks, these are methods of connecting network elements. LAN topology is the configuration of a graph, the vertices of which are computers or other equipment, and the arcs are physical connections between them. Configuration physical connections determined by electrical connections. It may differ from the configuration of logical connections, which are determined by data transmission routes through the configuration of communication equipment. The choice of a particular topology affects the composition of the equipment, network management methods, and the possibilities of network expansion. A passive topology is one in which devices do not regenerate the signal transmitted by the source. An example is bus and star topologies. In an active topology, devices regenerate a signal not intended for them and transmit it further. An example of an active topology is a ring. a b c Fig. 1 Basic topologies 8 Common bus In a network with a bus topology (Fig. 1, a), all devices are united by a single transmission medium. All workstations can communicate directly with any workstation on the network. The transmitted information can be distributed in both directions. The communication channel capacity is divided among all network nodes. Workstations can be connected to or disconnected from it at any time, without interrupting the operation of the entire computer network. The functioning of a computer network does not depend on the state of an individual workstation. Due to the fact that workstations can be turned on without interrupting network processes and the communication environment, it is very easy to eavesdrop on information, i.e. branch information from the communication environment. Pros: low cost and ease of wiring, no additional equipment required. Cons: low reliability and performance. A defective cable or connector paralyzes the entire network. Star The concept of a star-shaped network topology (Fig. 1, b) came from the field of mainframe computers, in which the head machine receives and processes all data from peripheral devices as an active data processing node. All information between two peripheral workstations passes through the central node of the computer network. Network throughput is determined by the computing power of the node and is guaranteed for each workstation. Cabling is quite simple as each workstation is connected to a node. Cabling costs are high, especially when the central node is not geographically located in the center of the topology. When expanding computer networks to a new workplace, it is necessary to lay a separate cable from the center of the network. The star topology is the fastest of all computer network topologies, since data transfer between workstations passes through a central node (if its performance is good) over separate lines used only by these workstations. The frequency of requests for information transfer from one station to another is low compared to that achieved in other topologies. The performance of a computer network primarily depends on the power of the central node. He might be bottleneck computer network. If the central node fails, the operation of the entire network is disrupted. The central control node can implement the optimal protection mechanism against unauthorized access to information. The entire computer network can be controlled from its center. Pros: higher throughput, ease of connecting new nodes, higher security against eavesdropping. Disadvantages: dependence of performance on the condition of the center, high cable consumption, higher cost. 9 Ring With a ring network topology (Fig. 1, c), workstations are connected to one another in a circle, i.e. workstation 1 with workstation 2, workstation 3 with workstation 4, etc. The last workstation is connected to the first. The communication link is closed in a ring. Currently, instead of a pairwise connection, a central device is used, inside of which a ring topology is implemented. This device can be active and regenerate the signal, or it can simply be a switch. Laying cables from one workstation to another can be quite complex and expensive, especially if the workstations are geographically located far from the ring (for example, in a line). Messages circulate regularly in circles. The workstation sends information to a specific destination address, having previously received a request from the ring. Message forwarding is very efficient since most messages can be sent "on the road" over the cable system one after another. It is very easy to make a ring request to all stations. The duration of information transfer increases in proportion to the number of workstations included in the computer network. The main problem with a ring topology is that each workstation must actively participate in the transfer of information, and if at least one of them fails, the entire network is paralyzed. Faults in cable connections are easily localized. Connecting a new workstation requires a short-term shutdown of the network, since the ring must be open during installation. There is no limitation on the length of a computer network, since it is ultimately determined solely by the distance between two workstations. Cons: low fault tolerance, breaking the network to add nodes. Table 2. Characteristics of computer network topologies Topology Characteristic Bus Star Ring Expansion cost Average Insignificant Average Subscriber connection Passive Passive Active Failure protection High Insignificant Insignificant System dimensions Limited Any Any Protection from pro- Insignificant Good Good eavesdropping System behavior under Bad Good Satisfactory high loads Ability to work in Poor Very good Good real time Cable routing Good Satisfactory Satisfactory 10
Definition. Information and computing network is a system of computers connected by data transmission channels.
Connecting computers into a network provides the following basic capabilities:
> Pooling of resources - the ability to reserve computing power and data transmission facilities in case of failure of some of them in order to quickly restore normal network operation.
> Resource sharing - the ability to stabilize and increase the load level of computers and expensive peripheral equipment, and manage peripheral devices.
> Data sharing - the ability to create distributed databases located in the memory of individual computers and manage them from peripheral workstations
> Software sharing - the ability to share software.
> Sharing of computing resources - the ability to organize parallel data processing; using other systems on the network to process data.
> Multi-user mode.
The main task of the IVS is information services for users, including:
Data storage and processing;
Providing data to users.
Modern information systems, as a rule, are distributed. Thus, an IVS is a complex of technical means that ensure the functioning of the IS (technical support subsystem).
IVS quality indicators:
Completeness functionality;
Performance(average number of requests processed per unit of time). An important performance indicator is throughput networks – the amount of data transmitted through the network per unit of time.
Reliability(resistance to interference and failures)
Information security transmitted over the network;
Transparency for the user - he must use network resources in the same way as the local resources of his own computer.
Scalability and versatility– the ability to expand the network without a significant decrease in performance, as well as the ability to connect and use a variety of hardware and software.
12.1. IWS architecture. Territorial and local computer networks. IVS protocols.
A conceptual description of a computer network is often referred to as architecture.
The concept of IVS architecture usually includes a description of the following elements:
Geometry of network construction (topology);
Data transfer protocols;
Technical support of information and computer networks.
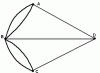
Definition. Topology- This is a diagram of the connection of network computers, cable systems and other network components.
IVS topologies are usually divided into 2 main classes:
broadcast;
consistent.
IN broadcast configurations each computer transmits signals that can be perceived by all other computers.
common bus;
tree (connection of common buses);
star with a passive center.
Broadcast topologies are used mainly for LANs.
IN sequential configurations Each physical sublayer transmits information to only one computer.
These configurations include:
hierarchical connection;
snowflake;
random connection (mesh configuration);
a star with an intellectual center;
Serial topologies are used for wide area networks.
Networks with bus topology use linear common channel communication, to which all nodes are connected through interface devices using short connecting lines.
Online with ring topology all nodes are connected into a single closed loop (ring) by communication channels. The output of one node is connected to the input of another node. Information is transmitted from node to node and, if necessary (if the message is not addressed to it), it is relayed further across the network. Data transfer is carried out using special interface equipment and is carried out in one direction.
The basis of the network with radial topology constitutes a special network device to which computers are connected - each via its own communication line. Such a device can be an active or passive hub, through which network workstations, for example, interact with the server.
There are also other types of topologies that are a development of the basic ones: chain, tree, snowflake, network, etc. The topology of a real network may coincide with one of the above, or be a combination of them.
Different topologies implement different principles of information transfer:
in broadcasting – selection of information;
in sequential ones – information routing.
IVS are classified according to a number of criteria. Depending on the distances between connected nodes, computer networks are distinguished:
territorial- covering a significant geographical location. Among territorial networks, one can distinguish regional and global networks, having regional or global scales, respectively; regional networks are sometimes called MAN (Metropolitan Area Network) networks, and the common English name for territorial networks is WAN (Wide Area Network);
local (LAN)- covering a limited area (usually within the distance of stations less than a few 10s or hundreds of meters from each other, less often - 1.2 km). Local area networks stand for LAN (Local Area Network);
Definition. Network protocol is a set of rules and methods for the interaction of computer network objects, covering basic procedures, algorithms and formats for converting and transmitting data in the network.
The International Organization for Standardization has developed a system of standard protocols that cover all levels of network interaction - from physical to application. This protocol system is called the Open System Interconnection (OSI) model.
The OSI model includes 7 layers of interaction:
1 – physical (forms a physical data transmission medium). Example: Ethernet;
2 – channel (organization and management of a physical data transmission channel);
3 – network (provides routing of data transmission in the network, establishes a logical data transmission channel). Example: IP;
4 – transport (provides segmentation of data and its reliable transmission from source to consumer). Example: TCP;
5 – sessional (initializing communication sessions between applications, managing queues and data transfer modes) Example:RPC;
6 – Presentations (provides a presentation of the transmitted data in a convenient way for application programs in the form, including encryption/decryption, syntax, etc.) Practical Application limited;
7 – applied (provides network access facilities for application programs). Example: FTP, HTTP, Telnet.
The Gaussian method has a number of disadvantages: it is impossible to know whether the system is consistent or not until all the transformations necessary in the Gaussian method have been carried out; Gauss's method is not suitable for systems with letter coefficients.
Let's consider other methods for solving systems linear equations. These methods use the concept of matrix rank and reduce the solution to any joint system to the solution of a system to which Cramer's rule applies.
Example 1. Find general solution next system linear equations using fundamental system solutions of the reduced homogeneous system and a particular solution of the inhomogeneous system.
1. Making a matrix A and extended system matrix (1)


2. Explore the system (1) for togetherness. To do this, we find the ranks of the matrices A and https://pandia.ru/text/78/176/images/image006_90.gif" width="17" height="26 src=">). If it turns out that , then the system (1) incompatible. If we get that , then this system is consistent and we will solve it. (The compatibility study is based on the Kronecker-Capelli theorem).
a. We find rA.
To find rA, we will consider sequentially non-zero minors of the first, second, etc. orders of the matrix A and the minors surrounding them.
M1=1≠0 (take 1 from the left top corner matrices A).
We border M1 the second row and second column of this matrix.  . We continue to border M1 the second line and the third column..gif" width="37" height="20 src=">. Now we border the non-zero minor M2′ second order.
. We continue to border M1 the second line and the third column..gif" width="37" height="20 src=">. Now we border the non-zero minor M2′ second order.
We have:  (since the first two columns are the same)
(since the first two columns are the same)
 (since the second and third lines are proportional).
(since the second and third lines are proportional).
We see that rA=2, a is the basis minor of the matrix A.
b. We find.
Fairly basic minor M2′ matrices A border with a column of free terms and all rows (we have only the last row).
 . It follows that M3′′ remains the basic minor of the matrix https://pandia.ru/text/78/176/images/image019_33.gif" width="168 height=75" height="75"> (2)
. It follows that M3′′ remains the basic minor of the matrix https://pandia.ru/text/78/176/images/image019_33.gif" width="168 height=75" height="75"> (2)
Because M2′- basis minor of the matrix A systems (2) , then this system is equivalent to the system (3) , consisting of the first two equations of the system (2) (for M2′ is in the first two rows of matrix A).
 (3)
(3)
Since the basic minor https://pandia.ru/text/78/176/images/image021_29.gif" width="153" height="51"> (4)
In this system there are two free unknowns ( x2 And x4 ). That's why FSR systems (4) consists of two solutions. To find them, we assign free unknowns in (4) values first x2=1 , x4=0 , and then - x2=0 , x4=1 .
At x2=1 , x4=0 we get:
 .
.
This system already has the only thing solution (it can be found using Cramer's rule or any other method). Subtracting the first from the second equation, we get:
Her solution will be x1= -1 , x3=0 . Given the values x2 And x4 , which we gave, we get the first fundamental solution systems (2) : .
Now we believe in (4) x2=0 , x4=1 . We get:
 .
.
We solve this system using Cramer’s theorem:

 .
.
We obtain the second fundamental solution of the system (2) : .
Solutions β1 , β2 and make up FSR systems (2) . Then its general solution will be
γ= C1 β1+С2β2=С1(‑1, 1, 0, 0)+С2(5, 0, 4, 1)=(‑С1+5С2, С1, 4С2, С2)
Here C1 , C2 – arbitrary constants.
4. Let's find one private solution heterogeneous system(1) . As in paragraph 3 , instead of the system (1) Let's consider an equivalent system (5) , consisting of the first two equations of the system (1) .
 (5)
(5)
Let us move the free unknowns to the right sides x2 And x4.
 (6)
(6)
Let's give free unknowns x2 And x4 arbitrary values, for example, x2=2 , x4=1 and put them in (6) . Let's get the system

This system has the only solution(since its determinant M2′0). Solving it (using Cramer’s theorem or Gauss’s method), we obtain x1=3 , x3=3 . Given the values of the free unknowns x2 And x4 , we get particular solution of an inhomogeneous system(1)α1=(3,2,3,1).
5. Now all that remains is to write it down general solution α of an inhomogeneous system(1) : it is equal to the sum private solution this system and general solution of its reduced homogeneous system (2) :
α=α1+γ=(3, 2, 3, 1)+(‑С1+5С2, С1, 4С2, С2).
This means:  (7)
(7)
6. Examination. To check if you solved the system correctly (1) , we need a general solution (7) substitute in (1) . If each equation turns into the identity ( C1 And C2 must be destroyed), then the solution is found correctly.
We'll substitute (7) for example, only the last equation of the system (1) (x1 + x2 + x3 ‑9 x4 =‑1) .
We get: (3–С1+5С2)+(2+С1)+(3+4С2)–9(1+С2)=–1
(С1–С1)+(5С2+4С2–9С2)+(3+2+3–9)=–1
Where –1=–1. We got an identity. We do this with all the other equations of the system (1) .
Comment. The check is usually quite cumbersome. The following “partial check” can be recommended: in the general solution of the system (1) assign some values to arbitrary constants and substitute the resulting partial solution only into the discarded equations (i.e., into those equations from (1) , which were not included in (5) ). If you get identities, then more likely, system solution (1) found correctly (but such a check does not provide a complete guarantee of correctness!). For example, if in (7) put C2=- 1 , C1=1, then we get: x1=-3, x2=3, x3=-1, x4=0. Substituting into the last equation of system (1), we have: - 3+3 - 1 - 9∙0= - 1 , i.e. –1=–1. We got an identity.
Example 2. Find a general solution to a system of linear equations (1) , expressing the basic unknowns in terms of free ones.
Solution. As in example 1, compose matrices A and https://pandia.ru/text/78/176/images/image010_57.gif" width="156" height="50"> of these matrices. Now we leave only those equations of the system (1) , the coefficients of which are included in this basic minor (i.e., we have the first two equations) and consider the system consisting of them, equivalent system (1).
Let us transfer the free unknowns to the right-hand sides of these equations.
system (9) We solve by the Gaussian method, considering the right-hand sides as free terms.
https://pandia.ru/text/78/176/images/image035_21.gif" width="202 height=106" height="106">

Option 2.

https://pandia.ru/text/78/176/images/image039_16.gif" width="192" height="106 src=">

Option 4.
https://pandia.ru/text/78/176/images/image042_14.gif" width="172" height="80">
Option 5.
https://pandia.ru/text/78/176/images/image044_12.gif" width="179 height=106" height="106">
Option 6.
https://pandia.ru/text/78/176/images/image046_11.gif" width="195" height="106">
Example 1. Find a general solution and some fundamental system of solutions for the systemSolution find using a calculator. The solution algorithm is the same as for systems of linear not homogeneous equations.
Operating only with rows, we find the rank of the matrix, the basis minor; We declare dependent and free unknowns and find a general solution.

The first and second lines are proportional, let’s cross out one of them:
 .
.
Dependent variables – x 2, x 3, x 5, free – x 1, x 4. From the first equation 10x 5 = 0 we find x 5 = 0, then
The general solution is:

We find a fundamental system of solutions, which consists of (n-r) solutions. In our case, n=5, r=3, therefore, the fundamental system of solutions consists of two solutions, and these solutions must be linearly independent. For the rows to be linearly independent, it is necessary and sufficient that the rank of the matrix composed of the elements of the rows be equal to the number of rows, that is, 2. It is enough to give the free unknowns x 1 and x 4 values from the rows of the second-order determinant, nonzero, and calculate x 2 , x 3 , x 5 . The simplest non-zero determinant is .
So the first solution is:
These two decisions constitute a fundamental decision system. Note that the fundamental system is not unique (you can create as many nonzero determinants as you like).
Example 2. Find the general solution and fundamental system of solutions of the system 
Solution.

 ,
,
it follows that the rank of the matrix is 3 and equal to the number unknown. This means that the system does not have free unknowns, and therefore has a unique solution - a trivial one.
Exercise . Explore and solve a system of linear equations.
Example 4
Exercise . Find the general and particular solutions of each system.
Solution. Let's write down the main matrix of the system:
| 5 | -2 | 9 | -4 | -1 |
| 1 | 4 | 2 | 2 | -5 |
| 6 | 2 | 11 | -2 | -6 |
| x 1 | x 2 | x 3 | x 4 | x 5 |
Let's reduce the matrix to triangular view. We will work only with rows, since multiplying a matrix row by a number other than zero and adding it to another row for the system means multiplying the equation by the same number and adding it with another equation, which does not change the solution of the system.
Multiply the 2nd line by (-5). Let's add the 2nd line to the 1st:
| 0 | -22 | -1 | -14 | 24 |
| 1 | 4 | 2 | 2 | -5 |
| 6 | 2 | 11 | -2 | -6 |
Let's multiply the 2nd line by (6). Multiply the 3rd line by (-1). Let's add the 3rd line to the 2nd:
Let's find the rank of the matrix.
| 0 | 22 | 1 | 14 | -24 |
| 6 | 2 | 11 | -2 | -6 |
| x 1 | x 2 | x 3 | x 4 | x 5 |
The highlighted minor has highest order(of possible minors) and is nonzero (it equal to the product elements on the reverse diagonal), hence rank(A) = 2.
This minor is basic. It includes coefficients for the unknowns x 1 , x 2 , which means that the unknowns x 1 , x 2 are dependent (basic), and x 3 , x 4 , x 5 are free.
Let's transform the matrix, leaving only the basis minor on the left.
| 0 | 22 | 14 | -1 | -24 |
| 6 | 2 | -2 | -11 | -6 |
| x 1 | x 2 | x 4 | x 3 | x 5 |
The system with the coefficients of this matrix is equivalent to the original system and has the form:
22x 2 = 14x 4 - x 3 - 24x 5
6x 1 + 2x 2 = - 2x 4 - 11x 3 - 6x 5
Using the method of eliminating unknowns, we find non-trivial solution:
We obtained relations expressing the dependent variables x 1 , x 2 through the free ones x 3 , x 4 , x 5 , that is, we found general solution:
x 2 = 0.64x 4 - 0.0455x 3 - 1.09x 5
x 1 = - 0.55x 4 - 1.82x 3 - 0.64x 5
We find a fundamental system of solutions, which consists of (n-r) solutions.
In our case, n=5, r=2, therefore, the fundamental system of solutions consists of 3 solutions, and these solutions must be linearly independent.
For the rows to be linearly independent, it is necessary and sufficient that the rank of the matrix composed of row elements be equal to the number of rows, that is, 3.
It is enough to give the free unknowns x 3 , x 4 , x 5 values from the lines of the 3rd order determinant, non-zero, and calculate x 1 , x 2 .
The simplest non-zero determinant is the identity matrix.
| 1 | 0 | 0 |
| 0 | 1 | 0 |
| 0 | 0 | 1 |
Task . Find a fundamental set of solutions to a homogeneous system of linear equations.
A system of linear equations in which everything free members are equal to zero are called homogeneous :
Any homogeneous system is always consistent, since it always has zero (trivial ) solution. The question arises under what conditions will a homogeneous system have a nontrivial solution.
Theorem 5.2.A homogeneous system has a nontrivial solution if and only if the rank of the main matrix less number her unknowns.
Consequence. A square homogeneous system has a nontrivial solution if and only if the determinant of the main matrix of the system is not equal to zero.
Example 5.6. Determine the values of the parameter l at which the system has nontrivial solutions, and find these solutions:

Solution. This system will have a non-trivial solution when the determinant of the main matrix is equal to zero:
Thus, the system is non-trivial when l=3 or l=2. For l=3, the rank of the main matrix of the system is 1. Then, leaving only one equation and assuming that y=a And z=b, we get x=b-a, i.e.
For l=2, the rank of the main matrix of the system is 2. Then, choosing the minor as the basis:
![]()
we get a simplified system
From here we find that x=z/4, y=z/2. Believing z=4a, we get
The set of all solutions of a homogeneous system has a very important linear property : if columns X 1 and X 2 - solutions to a homogeneous system AX = 0, then any linear combination of them a X 1 + b X 2 will also be a solution to this system. Indeed, since AX 1 = 0 And AX 2 = 0 , That A(a X 1 + b X 2) = a AX 1 + b AX 2 = a · 0 + b · 0 = 0. It is because of this property that if a linear system has more than one solution, then there will be an infinite number of these solutions.
Linearly independent columns E 1 , E 2 , Ek, which are solutions of a homogeneous system, are called fundamental system of solutions homogeneous system of linear equations if the general solution of this system can be written as a linear combination of these columns:
If a homogeneous system has n variables, and the rank of the main matrix of the system is equal to r, That k = n-r.
Example 5.7. Find the fundamental system of solutions to the following system of linear equations:

Solution. Let's find the rank of the main matrix of the system:

Thus, the set of solutions to this system of equations forms linear subspace dimensions n-r= 5 - 2 = 3. Let’s choose minor as the base
![]() .
.
Then, leaving only the basic equations (the rest will be a linear combination of these equations) and the basic variables (we move the rest, the so-called free variables to the right), we obtain a simplified system of equations:

Believing x 3 = a, x 4 = b, x 5 = c, we find
![]() ,
, ![]() .
.
Believing a= 1, b = c= 0, we obtain the first basic solution; believing b= 1, a = c= 0, we obtain the second basic solution; believing c= 1, a = b= 0, we obtain the third basic solution. As a result, the normal fundamental system of solutions will take the form
Using the fundamental system, the general solution of a homogeneous system can be written as
X = aE 1 + bE 2 + cE 3. a
Let us note some properties of solutions to an inhomogeneous system of linear equations AX=B and their relationship with the corresponding homogeneous system of equations AX = 0.
General solution of an inhomogeneous systemis equal to the sum of the general solution of the corresponding homogeneous system AX = 0 and an arbitrary particular solution of the inhomogeneous system. Indeed, let Y 0 is an arbitrary particular solution of an inhomogeneous system, i.e. AY 0 = B, And Y- general solution of a heterogeneous system, i.e. AY=B. Subtracting one equality from the other, we get
A(Y-Y 0) = 0, i.e. Y-Y 0 is the general solution of the corresponding homogeneous system AX=0. Hence, Y-Y 0 = X, or Y=Y 0 + X. Q.E.D.
Let the inhomogeneous system have the form AX = B 1 + B 2 . Then the general solution of such a system can be written as X = X 1 + X 2 , where AX 1 = B 1 and AX 2 = B 2. This property expresses the universal property of any linear systems(algebraic, differential, functional, etc.). In physics this property is called superposition principle, in electrical and radio engineering - principle of superposition. For example, in the theory of linear electrical circuits the current in any circuit can be obtained as algebraic sum currents caused by each energy source separately.